

Socios & Patrocinadores
¿Interesado en co-branding / patrocinio? Contactar
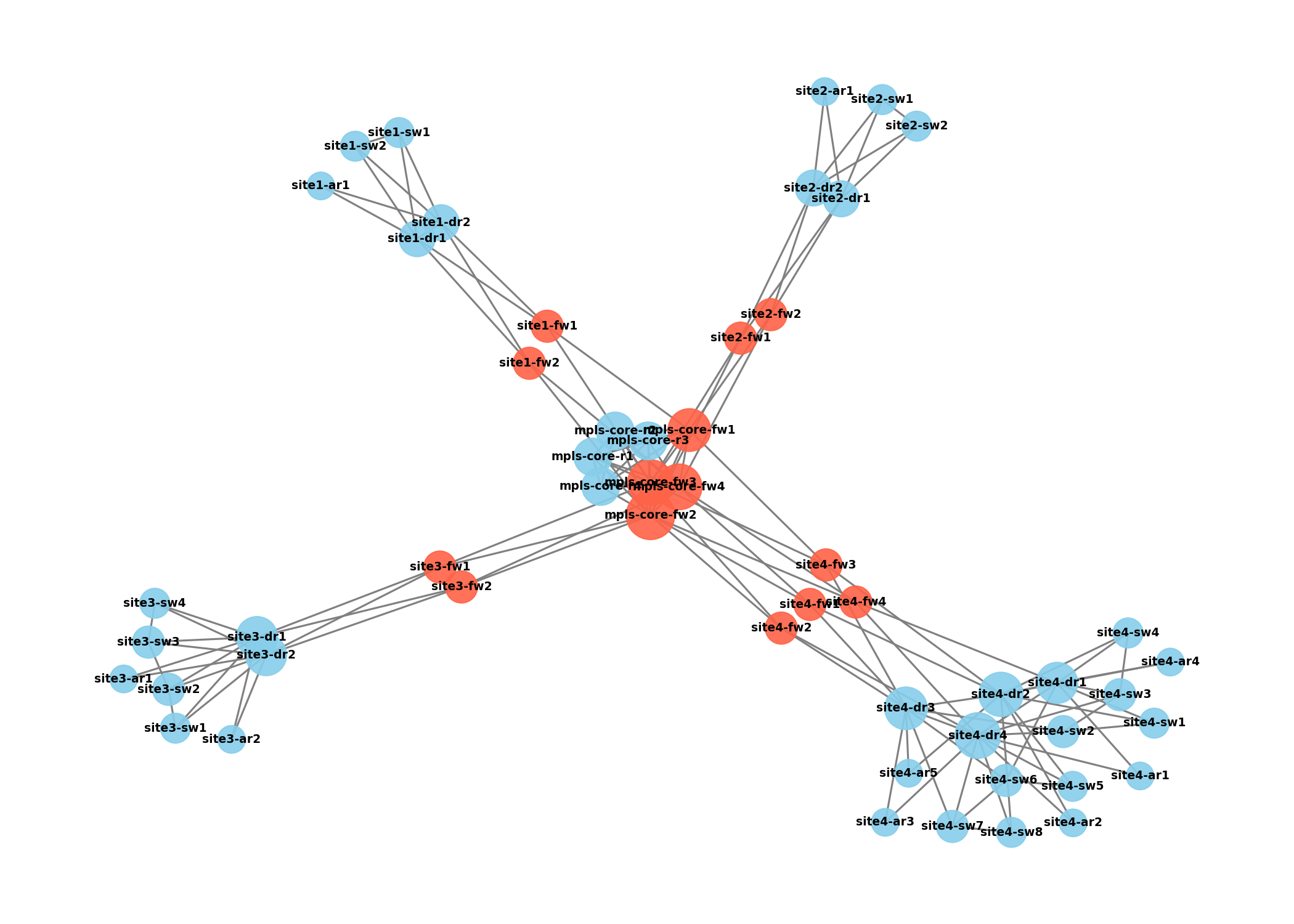
Este informe resume los principales hallazgos del análisis de las configuraciones de red y sistemas, teniendo en cuenta los requisitos relevantes de NIS2 y TISAX. La configuración de NTP, las políticas de contraseñas, los sistemas de registro (syslog) y las listas de control de acceso (ACL) son componentes esenciales de un ISMS robusto y determinantes para el cumplimiento normativo.
La red desempeña un papel fundamental: como la "columna vertebral de los datos" de toda organización, determina en gran medida cómo se transmiten, almacenan y gestionan de forma segura las informaciones. Una arquitectura de red estable y bien protegida constituye la base de medidas de seguridad eficaces y minimiza el riesgo de ataques o configuraciones erróneas.
| Device | Issue | Severity | Recommendation | Details |
|---|---|---|---|---|
| MPLS-Core-FW3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-DR2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-SW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW4 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site4-SW4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW7 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-FW2 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site4-FW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-DR4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-SW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-SW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-DR2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-FW1 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site3-FW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW5 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-DR1 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site1-DR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW3 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site4-SW3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-FW1 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site1-FW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-FW2 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site2-FW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-FW1 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site4-FW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW1 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site4-SW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-FW2 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site1-FW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-AR2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-AR3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-DR2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-FW4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-DR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW8 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-DR2 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site1-DR2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-R4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-DR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-R2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-AR4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-DR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-AR5 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-FW4 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site4-FW4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-AR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-SW3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-R3 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| MPLS-Core-R3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-FW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-SW6 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-R1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-SW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-AR1 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site1-AR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| MPLS-Core-FW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-SW4 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site1-SW2 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site1-SW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-AR2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-FW3 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site4-FW3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-AR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-SW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site2-FW1 | No NTP server configured | Warning | Configure at least one external NTP server for time sync | |
| Site2-FW1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site3-FW2 | Only 1 NTP server(s) configured | Info | Add second NTP server for redundancy | 4.4.4.4 |
| Site3-FW2 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-AR1 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client | |
| Site4-DR3 | NTP authentication is not enabled | Medium | Enable 'ntp authenticate', define trusted-key, and match keys on server/client |
| Device | Issue | Severity | Recommendation | Config_Line |
|---|---|---|---|---|
| Site2-DR2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-SW1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-SW4 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-SW7 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-FW2 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site2-SW2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-SW1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-DR2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-FW1 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site4-SW5 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-DR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-SW3 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-FW1 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site2-FW2 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site4-FW1 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site4-SW1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-SW2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-FW2 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site4-AR2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-AR3 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-DR2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-DR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-SW8 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-DR2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| MPLS-Core-R4 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site2-DR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| MPLS-Core-R2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-AR4 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-DR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-AR5 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-FW4 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site3-AR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-SW3 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| MPLS-Core-R3 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-SW6 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| MPLS-Core-R1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-SW2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-AR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-SW4 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site1-SW2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site3-AR2 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-FW3 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site2-AR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site2-SW1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site2-FW1 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site3-FW2 | ASA enable password without encryption | High | Use 'enable password |
enable password cisco encrypted |
| Site4-AR1 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS | |
| Site4-DR3 | Missing 'service password-encryption' (IOS) | Warning | Enable 'service password-encryption' on IOS |
| Device | Issue | Severity | Recommendation | Config_Line |
|---|
| Device | Issue | Severity | Recommendation | Details |
|---|---|---|---|---|
| Site4-FW2 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site4-FW2 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site4-FW2 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site3-FW1 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site3-FW1 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site3-FW1 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site1-FW1 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site1-FW1 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site1-FW1 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site2-FW2 | ISAKMP / IPSec using MD5 | Medium | Use SHA-256 oder höher | Regex found 'hash md5' |
| Site2-FW2 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site2-FW2 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site4-FW1 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site4-FW1 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site4-FW1 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site1-FW2 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site1-FW2 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site1-FW2 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site4-FW4 | ISAKMP / IPSec using MD5 | Medium | Use SHA-256 oder höher | Regex found 'hash md5' |
| Site4-FW4 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site4-FW4 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site4-FW3 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site4-FW3 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site4-FW3 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site2-FW1 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site2-FW1 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site2-FW1 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Site3-FW2 | ISAKMP / IPSec using SHA-1 | Medium | Use SHA-256 oder höher | Regex found 'hash sha' oder 'hash sha1' |
| Site3-FW2 | ISAKMP / IPSec using DH group5 (1536-bit) | Medium | Use DH group14 oder höher (2048-bit) | Regex found 'group 5' |
| Site3-FW2 | ISAKMP / IPSec lifetime abweichend (43200) | Info | Use lifetime 86400 (24h) oder passenden Wert laut Richtlinie | Regex found 'lifetime 43200' |
| Device | Issue | Severity | Recommendation | Details |
|---|---|---|---|---|
| Site3-FW1 | ASA failover partially configured | Info | Verify 'failover lan unit' or 'failover interface' config | |
| Site2-FW2 | ASA failover partially configured | Info | Verify 'failover lan unit' or 'failover interface' config | |
| Site4-FW1 | ASA failover partially configured | Info | Verify 'failover lan unit' or 'failover interface' config | |
| MPLS-Core-FW1 | ASA failover partially configured | Info | Verify 'failover lan unit' or 'failover interface' config | |
| Site2-FW1 | ASA failover partially configured | Info | Verify 'failover lan unit' or 'failover interface' config |
| Device | Issue | Severity | Recommendation | Details |
|---|
| Device | Issue | Severity | Recommendation | Config_Line |
|---|---|---|---|---|
| Site2-DR2 | Only one syslog server configured (IOS) | Info | Add second syslog server for redundancy | trap |
| Site3-SW1 | Logging trap set to 'debugging' (IOS) | Info | Consider using 'warnings' or 'errors' to reduce log noise | logging trap debugging |
| Site4-SW4 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-SW7 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site2-SW2 | No Syslog server configured (IOS) | Warning | Use 'logging host |
|
| Site2-SW2 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site1-SW1 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-SW5 | Logging trap set to 'debugging' (IOS) | Info | Consider using 'warnings' or 'errors' to reduce log noise | logging trap debugging |
| Site4-SW3 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site2-FW2 | No Syslog server configured (ASA) | Warning | Use 'logging host |
|
| Site2-FW2 | No 'logging trap' level set (ASA) | Info | Configure 'logging trap |
|
| Site4-SW1 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-SW2 | No Syslog server configured (IOS) | Warning | Use 'logging host |
|
| Site4-SW2 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-AR2 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-AR3 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-DR1 | Only one syslog server configured (IOS) | Info | Add second syslog server for redundancy | trap |
| Site4-SW8 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-AR4 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-AR5 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site3-AR1 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site3-SW3 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site4-SW6 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site3-SW2 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site1-AR1 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| MPLS-Core-FW1 | Logging trap set to 'debugging' (ASA) | Info | Consider using 'warnings' or 'errors' to reduce log noise | logging trap debugging |
| Site3-SW4 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site1-SW2 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site3-AR2 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site2-AR1 | No 'logging trap' level set (IOS) | Info | Configure 'logging trap |
|
| Site2-SW1 | Logging trap set to 'debugging' (IOS) | Info | Consider using 'warnings' or 'errors' to reduce log noise | logging trap debugging |
| Site4-AR1 | Logging trap set to 'debugging' (IOS) | Info | Consider using 'warnings' or 'errors' to reduce log noise | logging trap debugging |
| Device | Issue | Severity | Recommendation | Config_Line |
|---|---|---|---|---|
| Site2-DR2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site3-DR2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site1-DR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-AR2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-AR3 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-DR2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-DR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site1-DR2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| MPLS-Core-R4 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site2-DR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| MPLS-Core-R2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-AR4 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site3-DR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-AR5 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site3-AR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| MPLS-Core-R3 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| MPLS-Core-R1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site1-AR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site3-AR2 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site2-AR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-AR1 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
| Site4-DR3 | Telnet access enabled on vty | High | Use SSH instead: 'transport input ssh' | transport input telnet ssh |
Esta sección muestra cuántos flujos se perderían si un nodo específico fallara (LostFlows). Un valor > 0 indica un posible punto único de falla (SPOF).
Buenas noticias: No se perdió ningún flujo – aparentemente no existe ningún SPOF.
| NodeDown | FlowsOkBefore | FlowsOkAfter | LostFlows |
|---|
| Structure_Type | Structure_Name | Source_Lines | Is truly unused? |
|---|---|---|---|
| extended ipv4 access-list | UNUSED_ACL_2742 | configs/MPLS-Core-FW3.cfg:[53, 54] | Yes |
| extended ipv4 access-list | UNUSED_ACL_9 | configs/MPLS-Core-R3.cfg:[31, 32, 33, 34] | No |
| extended ipv4 access-list | UNUSED_ACL_4510 | configs/MPLS-Core-R4.cfg:[31, 32] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site1-FW1.cfg:[43, 44, 45, 46, 47] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site1-FW1.cfg:[34, 35, 36, 37, 38, 39, 40, 41] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site1-FW2.cfg:[43, 44, 45, 46, 47] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site1-FW2.cfg:[34, 35, 36, 37, 38, 39, 40, 41] | No |
| extended ipv4 access-list | UNUSED_ACL_3531 | configs/Site1-FW2.cfg:[49, 50] | Yes |
| extended ipv4 access-list | UNUSED_ACL_6472 | configs/Site2-DR1.cfg:[40, 41, 42] | No |
| extended ipv4 access-list | UNUSED_ACL_28 | configs/Site2-DR2.cfg:[43, 44, 45, 46] | No |
| extended ipv4 access-list | UNUSED_ACL_3798 | configs/Site2-DR2.cfg:[40, 41] | No |
| extended ipv4 access-list | UNUSED_ACL_5106 | configs/Site2-DR2.cfg:[48, 49, 50, 51] | Yes |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site2-FW1.cfg:[39, 40, 41, 42, 43] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site2-FW1.cfg:[33, 34, 35, 36, 37] | No |
| extended ipv4 access-list | UNUSED_ACL_4633 | configs/Site2-FW1.cfg:[45, 46] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site2-FW2.cfg:[41, 42, 43, 44, 45] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site2-FW2.cfg:[33, 34, 35, 36, 37, 38, 39] | No |
| extended ipv4 access-list | UNUSED_ACL_1040 | configs/Site2-FW2.cfg:[51, 52, 53] | No |
| extended ipv4 access-list | UNUSED_ACL_2047 | configs/Site2-FW2.cfg:[47, 48, 49] | Yes |
| extended ipv4 access-list | UNUSED_ACL_6754 | configs/Site3-AR2.cfg:[27, 28, 29, 30] | No |
| extended ipv4 access-list | UNUSED_ACL_9685 | configs/Site3-DR1.cfg:[52, 53] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site3-FW1.cfg:[42, 43, 44, 45, 46] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site3-FW1.cfg:[34, 35, 36, 37, 38, 39, 40] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site3-FW2.cfg:[43, 44, 45, 46, 47] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site3-FW2.cfg:[34, 35, 36, 37, 38, 39, 40, 41] | No |
| extended ipv4 access-list | UNUSED_ACL_2309 | configs/Site3-FW2.cfg:[49, 50] | Yes |
| extended ipv4 access-list | UNUSED_ACL_7010 | configs/Site4-AR1.cfg:[24, 25, 26] | Yes |
| extended ipv4 access-list | UNUSED_ACL_5765 | configs/Site4-AR3.cfg:[24, 25, 26, 27] | No |
| extended ipv4 access-list | UNUSED_ACL_6157 | configs/Site4-AR4.cfg:[24, 25] | Yes |
| extended ipv4 access-list | UNUSED_ACL_3841 | configs/Site4-DR2.cfg:[62, 63, 64] | No |
| extended ipv4 access-list | UNUSED_ACL_4313 | configs/Site4-DR3.cfg:[56, 57, 58] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site4-FW1.cfg:[43, 44, 45, 46, 47] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site4-FW1.cfg:[34, 35, 36, 37, 38, 39, 40, 41] | No |
| extended ipv4 access-list | UNUSED_ACL_6435 | configs/Site4-FW1.cfg:[49, 50, 51] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site4-FW2.cfg:[42, 43, 44, 45, 46] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site4-FW2.cfg:[34, 35, 36, 37, 38, 39, 40] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site4-FW3.cfg:[45, 46, 47, 48, 49] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site4-FW3.cfg:[34, 35, 36, 37, 38, 39, 40, 41, 42, 43] | No |
| extended ipv4 access-list | ACL_DMZ_OUTSIDE | configs/Site4-FW4.cfg:[43, 44, 45, 46, 47] | No |
| extended ipv4 access-list | ACL_INSIDE_DMZ | configs/Site4-FW4.cfg:[34, 35, 36, 37, 38, 39, 40, 41] | No |
| Node | Filter_Name | Flow | Action | Line_Content | Trace |
|---|
Sincronización NTP (Requisito TISAX p. ej. AL2.5 «Sello de tiempo», NIS2 Art. 20/21):
Una sincronización horaria precisa y confiable es esencial para el registro correcto
de eventos y la integridad de los sistemas. Solo así se pueden correlacionar
los incidentes de seguridad entre diferentes fuentes de logs.
Configuración Syslog (TISAX p. ej. AL2.5 «Logging & Monitoring», NIS2 Art. 20/21):
La recopilación y el análisis centralizados de los registros apoyan tanto a TISAX/ISMS
como a NIS2 (detección y reporte de incidentes).
También es esencial para el archivo seguro y rastreable de los logs.
Políticas de contraseñas (TISAX AL2.1.x «Password Policies», NIS2 Art. 21 «Access Control»):
Políticas de contraseñas complejas y aplicadas estrictamente son requisitos clave
en TISAX y NIS2 en cuanto a la gestión de usuarios e identidades.
Esto incluye longitud mínima, caracteres especiales, cambios regulares,
mecanismos de bloqueo y autenticación multifactor (MFA), según el nivel de riesgo.
Listas de control de acceso (ACL) (TISAX AL3 «Network Security Requirements», NIS2 Art. 21 «Segmentation»):
Las ACL permiten la segmentación y control de los flujos en la red.
Un uso insuficiente o incorrecto puede generar vulnerabilidades críticas.
TISAX exige segmentación clara y reglas de acceso; NIS2 también requiere
medidas técnicas y organizativas adecuadas para proteger la infraestructura.
Telnet vs. SSH (TISAX AL2.5 «Cifrado en tránsito», NIS2 Art. 20 «Ciberhigiene»):
Protocolos antiguos y sin cifrado como Telnet representan un riesgo significativo.
Tanto TISAX como NIS2 exigen accesos de gestión seguros — es decir, SSH en lugar de Telnet.
Esto asegura un nivel básico de cifrado y protección contra ataques de tipo Man-in-the-Middle.
IPSec / VPN (TISAX AL2.5 o AL3.3 «Criptografía», NIS2 Art. 20/21):
Conexiones VPN seguras mediante IPSec (p. ej. IKEv2 con AES-256 y DH Group14+) son esenciales
para proteger la comunicación entre sitios o accesos remotos.
TISAX requiere cifrado adecuado de datos en tránsito; NIS2 exige medidas eficaces
contra la interceptación y manipulación.
Servicios no utilizados (TISAX AL2.x «Hardening», NIS2 Art. 20 «Ciberhigiene»):
Los servicios o puertos innecesarios deben deshabilitarse sistemáticamente.
Esto reduce la superficie de ataque y dificulta que los atacantes aprovechen vulnerabilidades.
Tanto TISAX como NIS2 requieren revisiones y actualizaciones regulares de configuraciones.
Uso de VRF (TISAX AL3 «Separación de red», NIS2 Art. 21):
El Virtual Routing & Forwarding (VRF) permite separar lógicamente
tablas e instancias de enrutamiento. Es especialmente importante cuando
coexisten sistemas con diferentes niveles de protección.
Una configuración incorrecta puede generar brechas; VRF debe implementarse
según TISAX (AL3) y los requisitos de segmentación de NIS2.
Seguridad SNMP (TISAX AL2.5 «Gestión segura», NIS2 Art. 20):
Versiones antiguas de SNMP (v1, v2c) son inseguras (p. ej. cadenas en texto plano).
TISAX y NIS2 exigen protocolos modernos como SNMPv3 (cifrado y autenticación)
para prevenir accesos no autorizados o manipulaciones.
Punto único de falla (SPOF) & Redundancia (TISAX AL2.10 o AL3.2 «Gestión de contingencias», NIS2 Art. 21):
En un entorno de alta disponibilidad, los SPOF deben identificarse y
eliminarse siempre que sea posible.
TISAX exige planes de contingencia y conceptos de redundancia para garantizar continuidad.
NIS2 también enfatiza medidas adecuadas para la continuidad del negocio y
la resiliencia frente a interrupciones.
La siguiente tabla muestra cómo ciertas categorías de red y seguridad se relacionan con los requisitos de los principales estándares y directivas. Para ISO/IEC 27001 y ISO/IEC 27002 se utilizaron los números de la versión 2022.
| Categoría | ISO 27001:2022 (Anexo A) | ISO 27002:2022 | NIS2 (*1) | KRITIS (DE) | TISAX (VDA-ISA) | NIST (SP 800-53 / CSF) | CIS Controls (v8) | BSI IT-Grundschutz | Nota |
|---|---|---|---|---|---|---|---|---|---|
| Servidor de tiempo NTP | 8.17 (Sincronización del reloj) | 8.17 (Sincronización del reloj) | Art. 20, 21 (Detección, Registro) | §8a (IT-SiG) / KritisV | Proceso ISMS (AL2?), p. ej. « Sello de tiempo » | AU-8 (Sello de tiempo), CSF: DE.CM-7 (Monitoreo) | Control 8 (Gestión de registros de auditoría) | ORP.4 (Registro), SYS.1.1 | Los sellos de tiempo correctos son esenciales para la correlación de registros, la forensia y los eventos. |
| Políticas de contraseñas | 5.7 (Identificación & Autenticación), posiblemente 5.9 (Uso de acceso privilegiado) |
5.7 (Identificación & Autenticación), 5.9 (Uso de acceso privilegiado) |
Art. 21 (Control de acceso) | §8a (Acceso, Autentic.) | AL2.1.3 o AL2.2.2 (Políticas de contraseñas) | AC-2 (Gestión de cuentas), IA-5 (Auth), CSF: PR.AC |
Control 5 (Gestión de cuentas) | ORP.1 (Políticas), SYS.1.1 (Servidor) | Complejidad, longitud, bloqueo etc. reducen ataques de fuerza bruta y el uso indebido de accesos. |
| Configuración Syslog | 8.15 (Registro), 8.16 (Monitoreo de actividades) |
8.15 (Registro), 8.16 (Monitoreo) | Art. 20 (Registro), 21 | §8a BSI-G (Requisitos de registro) | AL2.5 (Monitoreo / Registro) | AU-2, AU-3 (Registro), CSF: DE.AE |
Control 8 (Gestión de registros de auditoría) | ORP.4 (Registro) | El registro centralizado (ej. Syslog) garantiza la integridad y simplifica el análisis. |
| Telnet / SSH | 5.35 (Uso de protocolos de comunicación seguros) | 5.35 (Uso de protocolos de comm. seguros) | Art. 20 (Medidas básicas de seguridad) | §8a / KritisV | AL2.5 (Cifrado en tránsito) | AC-17 (Acceso remoto), CSF: PR.AC |
Control 11 (Configuración segura) | NET.1.1 (Gestión segura) | SSH en lugar de Telnet (no cifrado) → Acceso remoto seguro. |
| Listas de control de acceso (ACL) | 8.23 (Seguridad de red) | 8.23 (Seguridad de red) | Art. 21 (Segmentación, Protección) | §8a / KritisV | AL3: « Requisitos de seguridad de red » | SC-7 (Protección de perímetro), CSF: PR.PT |
Control 9 (Puertos de red, Protocolos) | NET.1.1 (Routers/Switches) | Restricción de puertos/protocolos, segmentación, mínimos derechos de acceso. |
| IPSec / VPN | 5.31 (Uso de la criptografía), 5.35 (Comm. segura) |
5.31 (Uso de la criptografía), 5.35 |
Art. 20 (Criptografía), 21 | §8a / KritisV | AL2.5, AL3.3 (Requisitos criptográficos) | SC-13 (Protección criptográfica), CSF: PR.DS-2 |
Control 14 (Cifrado) | CON.2 (Concepto cripto), NET.1.1 | Conexiones VPN seguras, algoritmo fuerte (AES256, SHA-2, DH Group14+). |
| Conmutación por error ASA | 5.29 (Redundancia del procesamiento de la información) | 5.29 (Redundancia del procesamiento de la información) | Art. 21 (Gestión de riesgos, Resiliencia) | §8a BSI-G (Disponibilidad) | AL3.2 (Plan de emergencia?), AL2.10 (Redundancia) | CP-2, CP-10 (Contingencia, Redundancia), CSF: PR.IP-4 |
Control 12 / 13 (Continuidad del servicio) | SYS.4.1 (Conceptos de alta disponibilidad) | La conmutación por error y la redundancia son importantes para la disponibilidad y los requisitos KRITIS. |
| Servicios no utilizados | 8.9 (Gestión de configuración) | 8.9 (Gestión de configuración) | Art. 20 (Higiene cibernética) | §8a / KritisV | AL2.x (Endurecimiento?), Seguridad de software | CM-7 (Funcionalidad mínima), CSF: PR.IP-1 |
Control 2 (Inventario/Control SW) o 11 (Config segura) | SYS.1.1 (Servidor), NET.1.1 | Desactivar servicios no utilizados, minimizar la superficie de ataque. |
| ACL no utilizadas | 8.23 (Seguridad de red) | 8.23 (Seguridad de red) | Art. 21 (Seguridad de red) | §8a / KritisV | AL3 (Seguridad de red) | SC-7 (Protección de perímetro), CSF: PR.PT-3 |
Control 9 (Puertos de red, ACL) | NET.1.1, OPS.1.2 (Operación adecuada) | Eliminar reglas ACL innecesarias, reducir la complejidad, documentación clara. |
| Uso de VRF | 8.23 (Seguridad de red) | 8.23 (Seguridad de red) | Art. 21 (Segmentación) | §8a / KritisV | AL3 (Seguridad de red, Separación) | SC-7 (Protección de perímetro), CSF: PR.AC / PR.PT |
Control 9 (Limitación & Control) | NET.1.1 (Componentes de red) | Virtual Routing & Forwarding para separación lógica (clientes, zonas de seguridad, etc.). |
| Seguridad SNMP | 5.35 (Uso de protocolos de comm. seguros) | 5.35 (Uso de protocolos de comm. seguros) | Art. 20 (Protocolos de red seguros) | §8a / KritisV | AL2.5 (Cifrado en tránsito) | AC-17 (Gestión remota), CSF: PR.PT-3 |
Control 9.4 (Limitar protocolos de red) | NET.1.1 (Componentes de red) | SNMPv3 con Autenticación & Cifrado, no SNMPv1/v2c – reducción de riesgos MitM/sniffing. |
| Análisis SPOF | 5.29 (Redundancia) / posiblemente 5.30 (Resiliencia) | 5.29 / 5.30 (Resiliencia) | Art. 21 (Continuidad del negocio) | §8a / KritisV | AL2.10 o AL3.2 (Gestión de emergencias) | CP-2, CP-10 (Contingencia), CSF: ID.RA / PR.IP-9 |
Control 12 / 13 (Resiliencia, según versión) | SYS.4.1 (Alta disponibilidad), DER.3 (Gestión de incidentes) | Identificar puntos únicos de fallo, minimizar el riesgo de interrupción, estrategia de redundancia. |
(*1) Las referencias a artículos (Art. 20, Art. 21) corresponden a la Directiva NIS2 (UE) 2022/2555.
Nota: Esta tabla usa los números de control de ISO/IEC 27001:2022 y 27002:2022. Si su organización aún usa la versión 2013, los identificadores (A.x.x) serán distintos.
ISO 27001 se ha convertido en el «estándar de facto» en seguridad de la información. Basado en los controles de ISO 27002, se pueden evaluar medidas técnicas como logging, criptografía o segmentación de red. Las recomendaciones de este informe (políticas de contraseñas, ACLs, NTP, syslog) son esenciales para implementar correctamente dichos controles.
Los CIS Controls presentan una lista priorizada de medidas de ciberseguridad (inventario, control de accesos, monitoreo, etc.). Los CIS Benchmarks contienen recomendaciones detalladas de hardening para Cisco IOS, ASA, Linux o Windows. Los resultados de este informe pueden aplicarse directamente a las guías CIS.
Las directrices del NIST son ampliamente utilizadas en EE.UU. y a nivel internacional. El NIST Cybersecurity Framework (CSF) (con sus cinco funciones «Identify», «Protect», «Detect», «Respond» y «Recover») cubre requisitos técnicos y organizativos. Las debilidades de este informe (accesos inseguros, falta de monitoreo de logs) se ubican claramente en «Protect» y «Detect».
En Alemania, BSI IT-Grundschutz proporciona un marco obligatorio para medidas de seguridad. Componentes de red se encuentran en módulos como NET.1.1 (Routers & Switches) y SYS.1.1 (Servidores generales). Configuraciones seguras (p. ej. accesos cifrados de gestión, service password-encryption) ayudan significativamente a alcanzar los objetivos de IT-Grundschutz.
En el comercio electrónico, la norma PCI DSS es fundamental. Establece reglas estrictas para logging, segmentación de red, gestión de parches y cifrado con el fin de proteger los datos de tarjetas de crédito. Las debilidades identificadas en este informe (puertos Telnet abiertos, contraseñas sin cifrar) deben corregirse lo antes posible.
Para las organizaciones de salud (hospitales, IT médica), HIPAA es especialmente relevante. Auditorías, control de acceso y estándares de cifrado robustos son cruciales. Conexiones inseguras o configuraciones syslog deficientes pueden ocasionar violaciones en una auditoría HIPAA.
Existen además otros requisitos, entre ellos:
Para remediar las debilidades identificadas y fortalecer la seguridad de TI, se recomienda:
failover lan unit y failover interface).Estas medidas le ayudarán a cumplir mejor con TISAX y NIS2, además de otros marcos como ISO 27001/27002, CIS Benchmarks, NIST CSF, BSI IT-Grundschutz o KRITIS. Una red segura y bien configurada reduce significativamente la superficie de ataque y constituye un elemento clave de cualquier estrategia eficaz de ciberseguridad.